The Idea of Reduction
For problem $A$ and $B$, if there exists a computable function $f$ that for all instance $x\in A$, $A(x)=B(f(x))$, we say that $A$ could reduce to $B$.
Reduction (or simulation) is a powerful idea in computer science. Especially in cryptography, we use the idea of reduction to prove security of some cryptographic primitives.
We will illustrate the idea of reduction with a concrete example.
Example: Pseudo One-time Pad
Pseudo OTP:
Pseudo OTP solves OTP’s drawback that secret key $k$ needs to be as long as message $m$.
For $m\in {0,1}^n$, we expand a short key $k$ to the length $n$ with PRG: $r:=G(k)$. Pseudo OTP encrypts as $c:=m\oplus G(k)$.
Try to prove: Pseudo OTP $\Pi$ is EAV-secure if $G$ is a PRG.
We reduce “Pseudo OTP $\Pi$ is EAV-secure” to “$G$ is a PRG”.
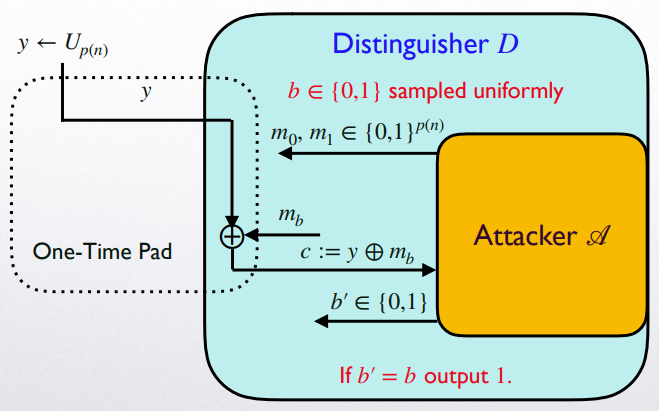
Construct a distinguisher $D$ for $G$ given $\mathscr{A}$ attacking $\Pi$ as its subroutine.
- $D$ runs $\mathscr{A}(1^n)$.
- $\mathscr{A}$ outputs $m_0,m_1$.
- $D$ generates a random bit $b\in{0,1}$ and obtain $r$ from PRG challenger.
- $D$ sends $m_b\oplus r$ back to $\mathscr{A}$.
- $\mathscr{A}$ finally outputs $b’$.
- If $b’=b$, $D$ outputs $1$, otherwise $0$.
Considering the following 2 cases:
$r\leftarrow U_{n}$ is truly random
In this case, the view of $\mathscr{A}$ is distributed identically to that of a true OTP protocol $\widetilde{\Pi}$ which obeys perfect secrecy, therefore $\Pr_{r\leftarrow U_{n}}[D(r)=1]=\Pr[b=b’]=\Pr[\mathtt{PrivK}^{eav}_{\mathscr{A}, \widetilde{\Pi}}(n)=1]=\frac{1}{2}$.
$r:=G(s)$ for some $s$ ($r$ is pseudorandom)
In this case, the view of $\mathscr{A}$ when run as a subroutine of $D$ is that of the adversarial indistinguishability experiment of the Pseudo OTP $\Pi$, therefore $\Pr_{s\leftarrow U_m}[D(G(s))=1]=\Pr[b=b’]=\Pr[\mathtt{PrivK}^{eav}_{\mathscr{A}, \Pi}(n)=1]$.
Reduction process:
Since $G$ is PRG: $|\Pr_{r\leftarrow U_{n}}[D(r)=1]-\Pr_{s\leftarrow U_m}[D(G(s))=1]|\leq \varepsilon(n)$.
From the 2 equality above: $|\Pr[\mathtt{PrivK}^{eav}{\mathscr{A}, \Pi}(n)=1]-\Pr[\mathtt{PrivK}^{eav}{\mathscr{A}, \widetilde{\Pi}}(n)=1]|\leq \varepsilon(n)$.
Therefore $\Pr[\mathtt{PrivK}^{eav}_{\mathscr{A}, \Pi}(n)=1]\leq \varepsilon(n)+\frac{1}{2}$, which indicates that pseudo OTP is EAV-secure.
Reduction Logic
Reduction provides an abstraction.
Understand the abstraction is the key to understand reduction.
If we want to reduce the security of $\Pi’$ to the security of $\Pi$, we need to construct an adversary $\mathscr{S}$ for $\Pi$ given the adversary $\mathscr{A}$ for $\Pi’$ as its subroutine, which is to say, $\mathscr{S}$ employs (runs) $\mathscr{A}$ as a black box abstraction function (Encapsulation).
The reduction involves 4 logic statements:
- $p:$ $\exists\ \mathscr{S}$ that is able to attack $\Pi$ with non-negligible advantage.
- $q:$ $\exists \ \mathscr{A}$ that is able to attack $\Pi’$ with non-negligible advantage.
- $\lnot p:$ $\Pi$ is secure, which means $\mathscr{S}$ that could successfully attack $\Pi$ is NOT exist.
- $\lnot q:$ $\Pi’$ is secure, which means $\mathscr{A}$ that could successfully attack $\Pi’$ is NOT exist.
If $\mathscr{S}$ is constructed successfully, it will be able to attack $\Pi$ with non-negligible advantage. Therefore we could conclude that if $\mathscr{A}$ could attack $\Pi’$ successfully, $\mathscr{S}$ (which takes $\mathscr{A}$ as its subroutine) could attack $\Pi$. The corresponding logic is $q\to p$.
According to the contrapositive statement, we have $\lnot p\to \lnot q$, which implys that the security of $\Pi$ guarantees the security of $\Pi’$. Therefore, the reduction is completed: we reduce the security of $\Pi’$ to the security of $\Pi$.
Contrapositive argument:
The contrapositive of the conditional statement “If $p$ then $q$. “ is “If not $q$ then not $p$”.
The logical equivalence could be expressed by $p\to q \iff \lnot q\to \lnot p$.
归约应该是整个密码学安全性证明中的核心思想之一。
第一次接触归约时 (即上文中提到的对伪一次性密码本安全性的证明) 真的思考了超级久才把整个逻辑捋清。但一旦想明白了就会觉得实在是巧妙:假设攻击方案 $A$ 的敌手存在,我们直接将该敌手封装 (encapsulate) 起来作为攻击已知安全的方案 $B$ 的敌手的子程序 (subroutine)。如果构建成功,根据逆否命题就能完成归约。
归约证明最难的地方应该在于 simulator $\mathscr{S}$ 的设计:其与子程序 $\mathscr{A}$ 的交互必须是黑盒式的,且无法让 $\mathscr{A}$ 察觉到与其互动的并不是 challenger $\mathscr{C}$,而是某个 simulator $\mathscr{S}$。
在整个课程的学习中了解到了很多很妙的归约,例如 Pseudorandom function/permutation 构建的加密方案的 CPA 安全性证明,Hash-MAC 与 Hash-Sign 方案的安全性证明,Authenticate encryption 的安全性证明,RSA 硬核谓词 (Hard-core predicates) 的证明,RSA-FDH (Full-Domain Hash) signature 的不可伪造性证明,Fiat-Shamir transformation 的证明,Schnorr identification 的安全性证明……
光是写出来就有一大串,就不具体介绍了 (我有一个绝妙的证明.jpg)